Discover and secure sensitive patient data
All-in-one vulnerability detection platform, with tailor-made compliancy features for the HealthTech industry.








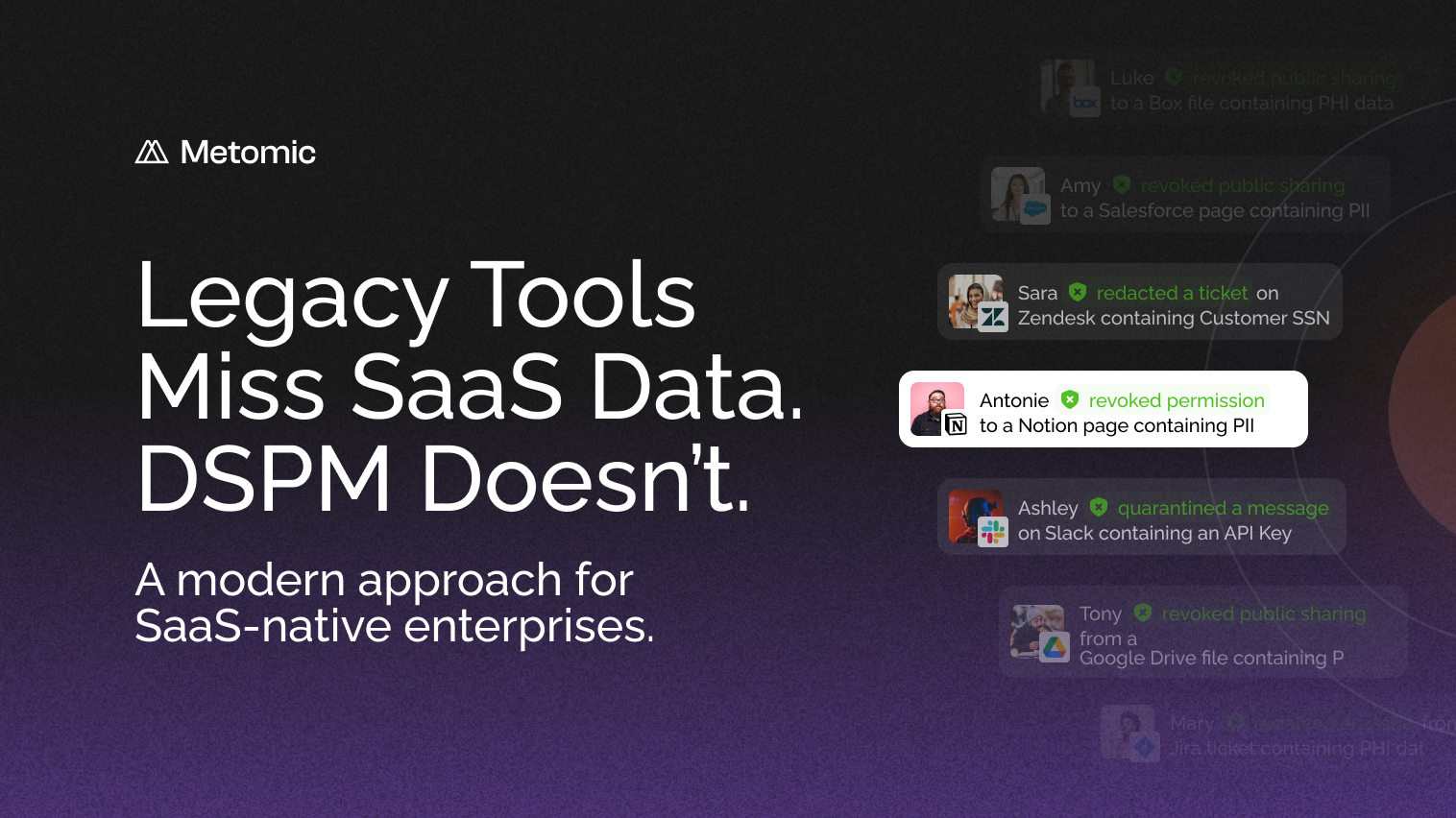
Prevent PHI being shared in riskySaaS environments
Tighten your security by accurately detecting PHI such as medical record numbers, scanned ID documents and more. We help you understand the most critical risks and you can put policies in place to automate the prevention of these in the future.
- Ready-to-use, automated HIPAA policies
- Extensive off-the-shelf classifiers
- Build your own classifiers for custom data
- Scan files and unstructured data



Metomic secures patient data across Numan's digital platforms
Read more about how Numan's Chief Medical Strategy Officer keeps sensitive patient data protected, using Metomic



How healthcare companies use Metomic
Healthcare companies around the world are using Metomic to secure customer data in SaaS apps. Here are a few ways you could use it to do the same:

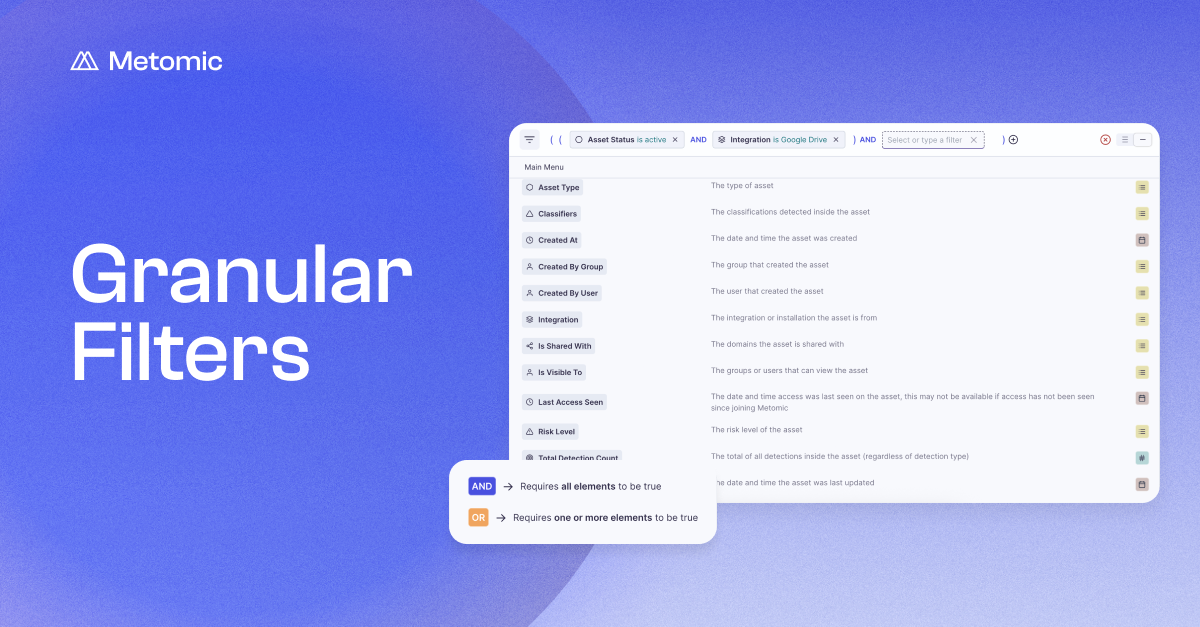
Data Discovery
Real-time and holistic visibility of sensitive data across your entire SaaS ecosystem

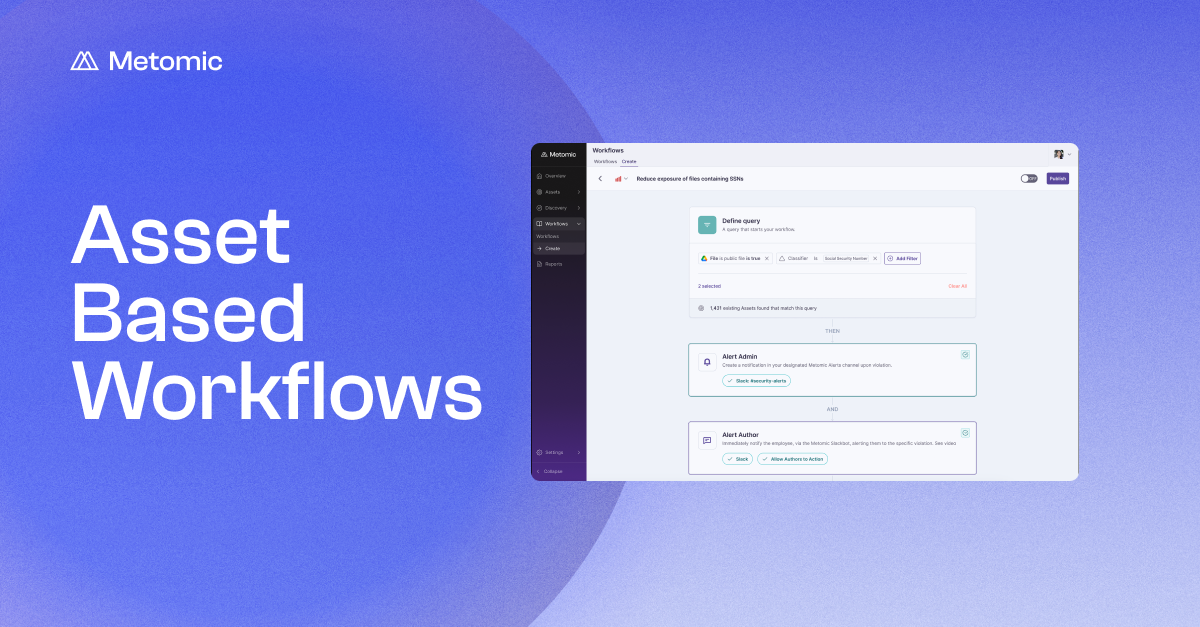
Data Loss Prevention
Automatically prevent specific data being shared in entire apps or isolated locations

Human Firewall
Enable the human firewall with real-time employee notifications when a policy has been violated

Access Controls
Control who has access to what data, and when - helping you reduce exposure in a few clicks

Insider Threat
Prevent insider threat with visibility and alerts for anomalous activities in any SaaS app

Compliance
Make your SaaS apps compliant with regulations and standards like HIPAA, PCI DSS, and GDPR
Trusted by organisations worldwide


_BestEstimatedROI_Mid-Market_Roi.png)
_HighPerformer_HighPerformer.png)


A non-corporate approach towards HealthTech Application Security
With Metomic, you’ll fast track your code & cloud security compliance while saving time and money.

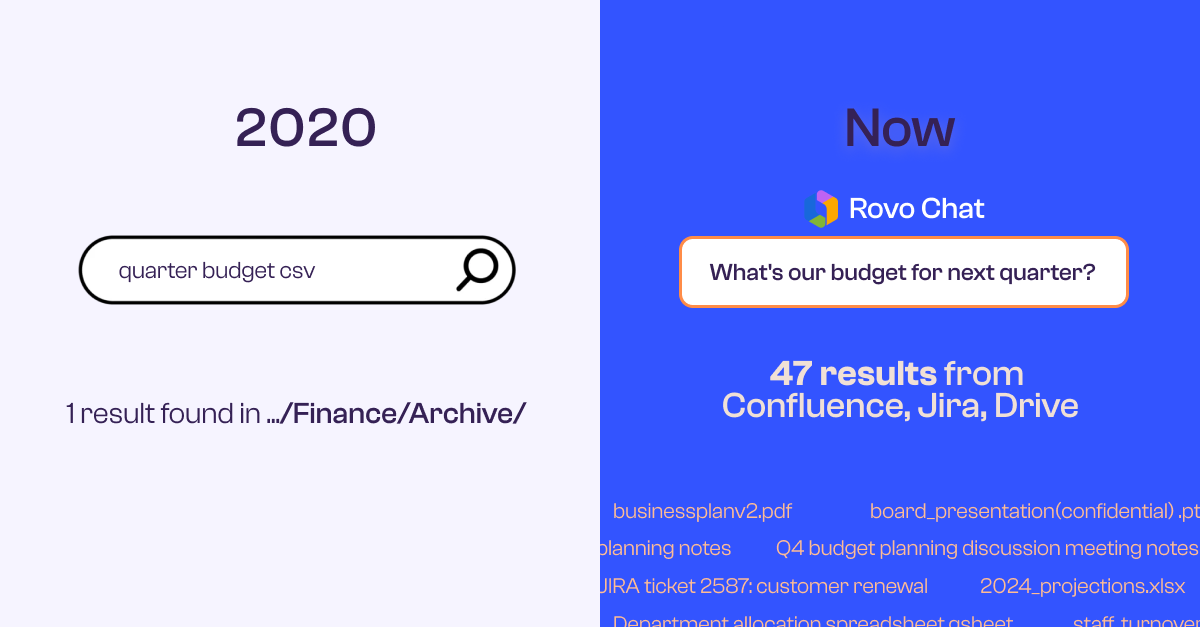
Data Security Insights for Healthcare

.png)








.png)








.jpg)


.png)

.png)








































































Book a Demo
Our team of security experts are on hand to walk you through the platform and show you the impact it can have on your business.
Simply fill in the form and we'll get back to you as soon as we can.


_BestEstimatedROI_Mid-Market_Roi.png)
_HighPerformer_HighPerformer.png)


