
Keep sensitive data in Dropbox safe
Metomic helps you detect, classify, and remediate sensitive files in real time. Streamline compliance, reduce breach risk, and free your security team from repetitive triage.
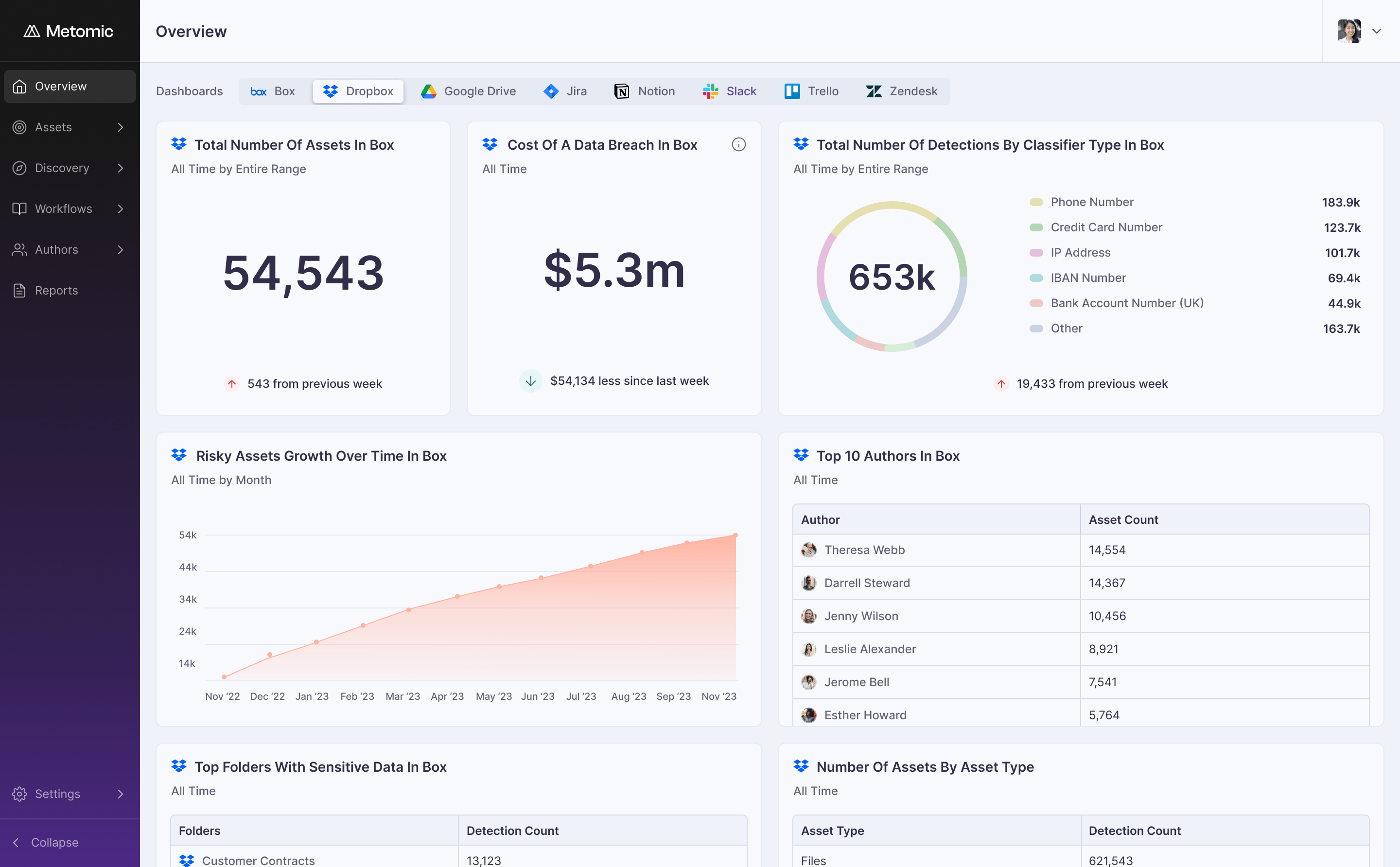

Gain true visibility over sensitive data stored in your Dropbox
Sensitive files in Dropbox often spread without control. We help you spot and stop risks before they become costly.
Metomic's data security software detects sensitive data in documents within Dropbox, helping you map out your most high-risk assets.
%201.png)
.png)

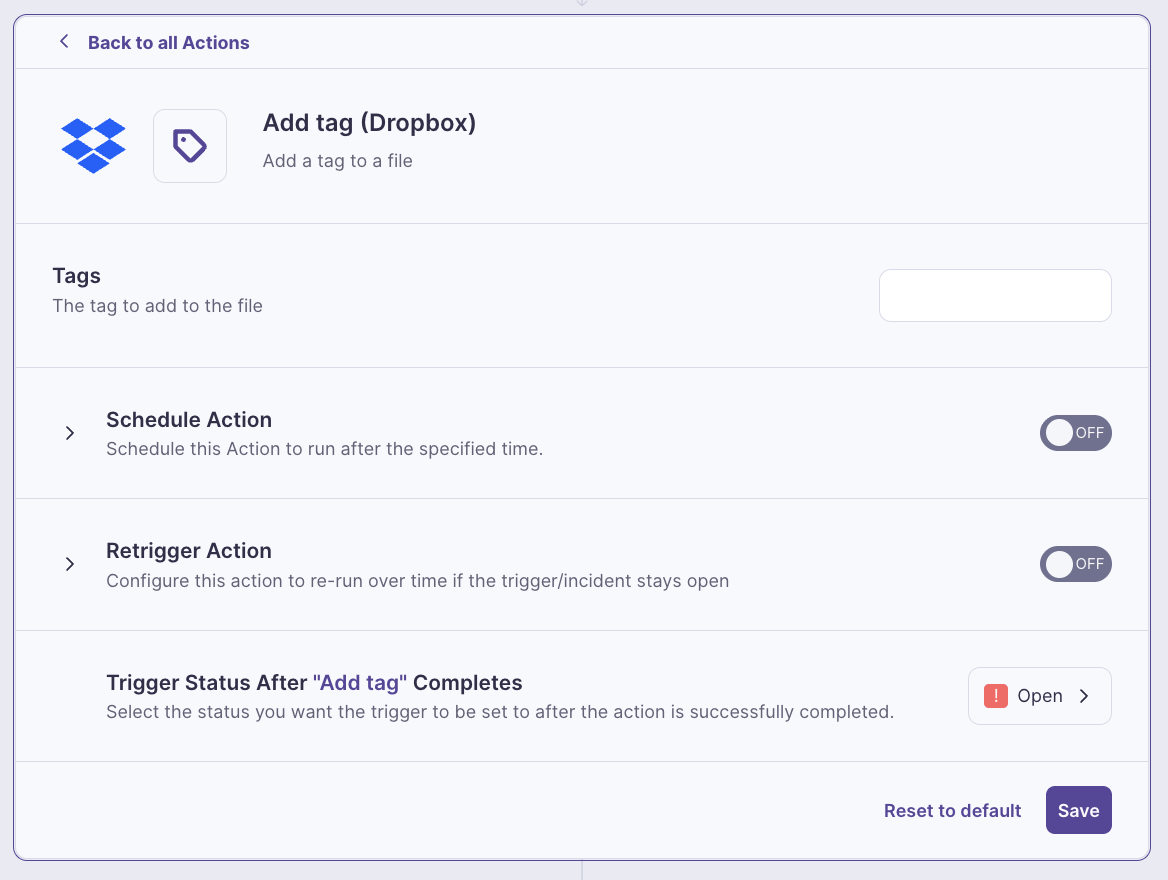
Automate policy enforcement and compliance
Sensitive data is hard to govern when policies depend on people. Metomic makes compliance automatic, so Dropbox stays secure without extra effort.
Metomic applies policies automatically to sensitive data, ensuring Dropbox files are governed in real time. From classification to remediation, compliance becomes a background process — not a manual burden.
- Classify and protect files the moment they’re shared
- Apply policies consistently with simple, flexible workflows
- Generate audit-ready reports without the manual grind
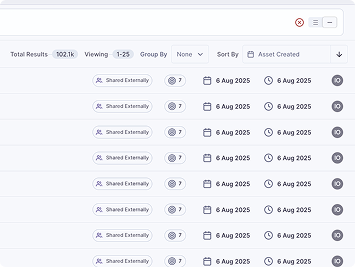

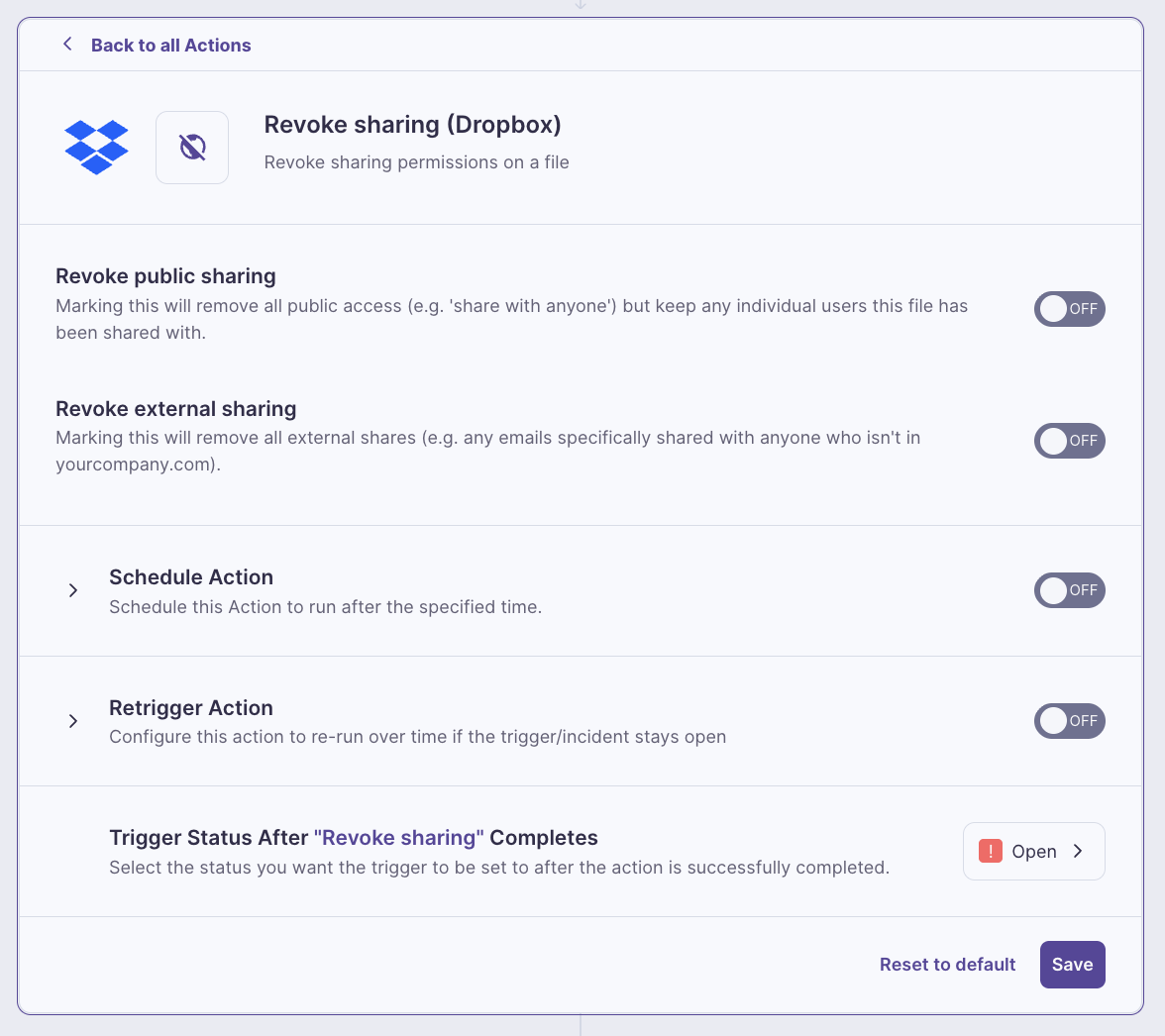
Reduce workload and cost across your security stack
Security teams shouldn’t waste time on repetitive reviews or juggling too many tools. Metomic keeps Dropbox protected while cutting down workload and spend.
Metomic automates low-value tasks and reduces false positives, freeing your team to focus on higher-value work. By streamlining operations, you lower costs and strengthen protection at the same time.
- Free your team from repetitive, low-value reviews
- Lower security costs without reducing coverage
- Scale protection without adding complexity

Learn more about SaaS data security
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Suspendisse varius enim in eros elementum tristique. Duis cursus, mi quis viverra ornare, eros dolor interdum nulla, ut commodo diam libero vitae erat. Aenean faucibus nibh et justo cursus id rutrum lorem imperdiet. Nunc ut sem vitae risus tristique posuere.

All your important questions, answered
How long does it take to get started?
Most teams are up and running in hours, not weeks. You can start with hundreds of out-of-the-box classifiers and add custom rules as you go.
Can I build my own custom rules?
Yes. You can use our ready-made workflows or create your own to spot the risks that matter most to your business.
Will this replace my existing security tools?
Often, yes. Many teams use Metomic to consolidate overlapping tools, reduce vendor sprawl, and cut costs — while improving protection at the same time.
Does Metomic slow down how my team uses Dropbox?
No. Metomic works in the background, detecting and protecting sensitive files in real time. Your team keeps using Dropbox exactly as they do today — without disruption or extra steps.
Book a personalised demo
Our team of security experts are on hand to walk you through the platform and show you the impact it can have on your business.
Simply fill in the form and we'll get back to you as soon as we can.


_BestEstimatedROI_Mid-Market_Roi.png)
_HighPerformer_HighPerformer.png)













.png)




.png)

.png)

.png)
.png)
.png)
.png)
.png)
.png)
.png)


.svg)

.png)
.png)
.png)
.png)
.png)
.png)