DSPM vs Legacy Data Security Tools
Legacy DSPM shows risks; Metomic resolves them. Continuous visibility, accurate classification, and automated remediation for cleaner audits and lower breach risk.
DSPM vs Legacy Data Security Tools
Legacy DSPM shows risks; Metomic resolves them. Continuous visibility, accurate classification, and automated remediation for cleaner audits and lower breach risk.

DSPM Isn’t New.
But the SaaS Environment You’re Securing Is.
According to the 2025 CSA “Understanding Data Security Risk” survey, nearly one in three organisations cannot identify their riskiest data sources, a gap that reflects outdated tooling and fragmented security strategies.
Legacy data-security designs struggle in distributed, cloud-native environments, leading to increased risk of leakage, misconfiguration, and governance failures.
Across this research, three challenges emerge consistently:
- Inability to locate and assess high-risk data across cloud and SaaS systems
The CSA report shows many organisations lack the tools or processes to reliably pinpoint where their most sensitive data actually resides. Without complete visibility, risk assessment becomes reactive, and often inaccurate. - Operational bottlenecks caused by fragmented workflows and manual effort
Cloud security teams frequently rely on disjointed, legacy controls that weren’t built for distributed data creation. This leads to manual investigations, inconsistent triage, and slow remediation cycles. - Fragmented security architectures that create blind spots across environments
Traditional on-prem approaches don’t extend cleanly into modern SaaS ecosystems. When teams are forced to stitch together multiple tools to cover cloud, SaaS, and collaboration platforms, gaps emerge — especially around governance, access, and real-time detection.
These issues share a common root cause: organisations are trying to secure cloud-era, SaaS-driven data with tooling designed for static, centralised environments. And as the research shows, that approach no longer works.
3 Main Challenges With Legacy Solutions
1. Discovery without ownership context
Most tools can tell you a file contains PII. Few can tell you who can see it or how widely it’s shared, and whether it’s already been synced into ten other tools.
Metomic’s unified asset model merges all that context into one place, giving CISOs the visibility they’ve been missing.
2. Classifiers that flood teams with noise
Generic classifiers create alert fatigue. Analysts spend hours chasing false positives or, worse, ignoring high-severity issues buried in the queue.
Metomic’s classifier library is tuned for SaaS behaviours, things like credentials in Slack, large datasets in Drive, regulated data in Jira. All of which can be customised by your engineering team for your environment.
3. “Fix it manually” isn’t a workflow
Identifying a risky file is one thing. Remediation is where DSPM tools usually fall apart.
Metomic automates the work security teams used to do by hand:
- Revoking public or external sharing
- Re-labelling files in Google Drive
- Redacting sensitive Slack messages
- Engaging employees directly to fix their own violations
It turns DSPM from a reporting function into an operational system.
Metomic’s DSPM Approach: Visibility, Precision, and Real Remediation
Unlike cloud-first DSPM vendors, Metomic was built for the messy, collaborative nature of SaaS environments.
Full-environment visibility through a single dashboard
Metomic continuously scans every connected SaaS tool and surfaces:
- where sensitive data lives
- how exposed it is
- who owns it
- how often it’s accessed or shared
The dashboards give CISOs a real-time risk picture they can take into a board meeting — without exporting CSVs or stitching insights from multiple tools.
.png)
High-precision classification that reduces noise instead of adding to it
Metomic’s classifiers identify PII, PHI, PCI, secrets, tokens, and other high-risk data types with accuracy tuned for collaboration tools.
Security teams can override or customise classifiers to match their governance model, and toggle out categories that don’t matter to their business. That keeps dashboards sharp and investigations focused.
Automated workflows that actually resolve risk
DSPM is only valuable if it changes outcomes. Metomic includes:
- Revoke internal, external, domain-wide, or public sharing
- Apply or correct Google Drive labels
- Redact content across SaaS tools
- Quarantine or restore files
- Notify users or managers directly via Slack or email
Each action can be triggered automatically, scheduled, or escalated only for certain severity levels.
This is where most DSPM tools stop short. Metomic goes further by ensuring incidents close automatically when the underlying risk is fixed — either by the system or by the employee.
Why Are CISOs Standardising DSPM Around SaaS Governance?
CISOs tell us the same thing: data risk isn’t coming from exotic attack paths. It’s coming from everyday usage of SaaS applications teams can’t operate without. In fact, a 2025 investigation found more than 660,000 misconfigured cloud storage buckets leaking over 200 billion files, underscoring how everyday operational use of cloud and SaaS, not sophisticated attacks, is now one of the most common causes of data exposure.
Metomic’s approach aligns to the pressures CISOs actually face:
Reduce breach risk without slowing down the business
Automated policies enforce guardrails quietly in the background, keeping productivity high while reducing accidental exposure.
Accelerate compliance cycles
Auditors want evidence of:
- consistent policies
- clear ownership
- accurate classification
- demonstrable remediation
Metomic generates audit-ready reports in minutes, not weeks.
Consolidate overlapping tools
Many organisations replace multiple DLP add-ons and manual review processes with Metomic’s unified DSPM + remediation system.
Prepare for AI adoption safely
As companies roll out AI agents across their SaaS stack, DSPM becomes the control plane preventing AI from ingesting or surfacing the wrong data. Metomic cleans up the environment first, then enforces guardrails continuously.
A Practical DSPM Blueprint Using Metomic Dashboards
CISOs typically follow a three-step pattern when deploying DSPM with Metomic:
1. Establish visibility and baseline exposure
Use Metomic’s Assets dashboard to:
- filter by exposure (public, external, internal)
- identify high-risk data types
- surface files with high detection counts
- map ownership and sharing behaviour
This creates the first defensible view of the real SaaS data footprint.
2. Enforce policies through automated workflows
Asset-based and event-based workflows allow CISOs to operationalise policy:
- PCI cannot be stored in publicly shared Drive files
- Slack credentials must be redacted immediately
- Drive labels must remain accurate
- Mass downloads trigger alerts
Workflows act as always-on governance, not point-in-time scanning.
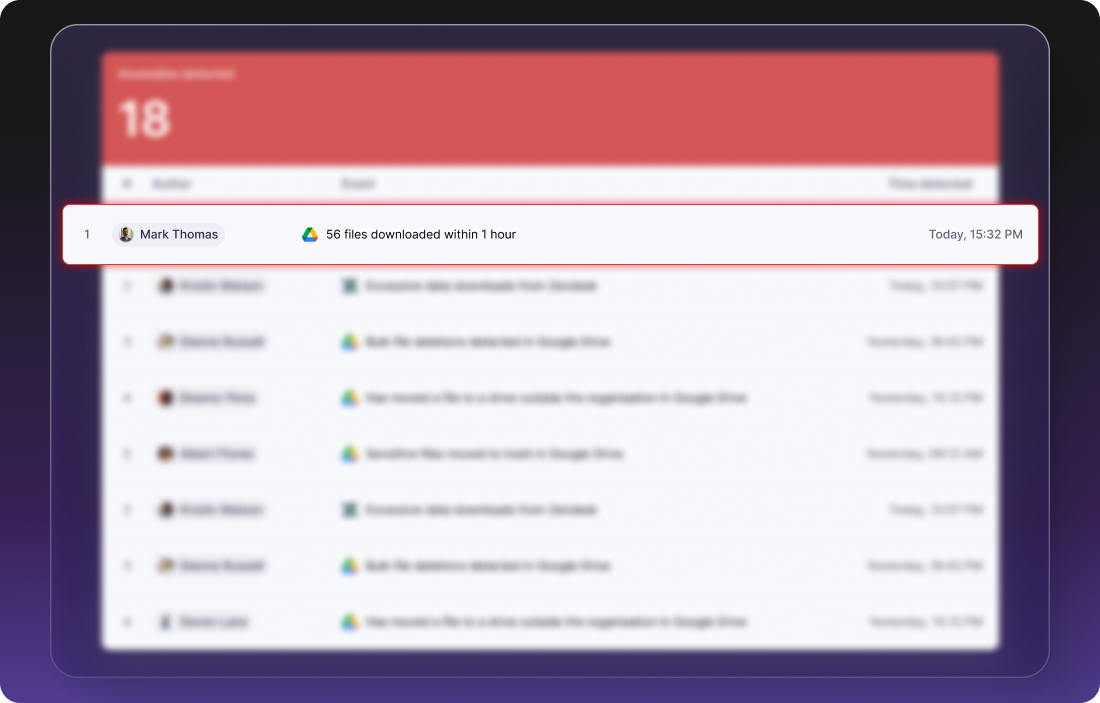
3. Remediate historical sprawl
Workflow Jobs allow bulk remediation — revoking sharing across hundreds or thousands of assets at once.
This transforms previously unmanageable data sprawl into a clean, governed starting point for AI, compliance, and growth.
The Future of DSPM Is Operational
Security leaders don’t need another dashboard showing them they have too much exposed data. They need a system that:
- discovers risk with precision
- provides full context
- fixes the exposure
- keeps it fixed
Metomic delivers this by treating DSPM as an active governance layer — continuously monitoring, classifying, and correcting risk across the SaaS tools where sensitive data is created and shared every day.
If you want DSPM your analysts will actually use, and your board will clearly understand, this is the approach that works.
Schedule a demo with Metomic to see it in action.



