DSPM Solutions in the US: Complete Guide for 2026
The US market leads global DSPM adoption, driven by stringent compliance requirements, high breach costs, and advanced cloud maturity. Find out the essential DSPM strategy for 2026.

DSPM Solutions in the US: Complete Guide for 2026
The US market leads global DSPM adoption, driven by stringent compliance requirements, high breach costs, and advanced cloud maturity. Find out the essential DSPM strategy for 2026.

Main Takeaways from This Article
- By 2026, Gartner projects that 20% of businesses will prioritize DSPM technologies to discover and secure data repositories across multi-cloud environments
- DSPM is the "heart of managing data security" in complex multi-cloud environments, particularly for identifying ‘shadow data’ that traditional tools miss, according to Gartner.
- The US leads global DSPM adoption, accounting for approximately 40% of the worldwide market as organizations shift from infrastructure-first to data-first security strategies
- AI and unstructured data protection have emerged as critical drivers, with organizations requiring automated classification across cloud, SaaS, and on-premises environments
- Regulatory compliance mandates including GDPR, HIPAA, and CCPA are accelerating DSPM adoption as enterprises must demonstrate comprehensive data visibility and governance
What is DSPM (Data Security Posture Management)?
Data Security Posture Management (DSPM) represents a fundamental shift in how organizations approach cloud data security. Unlike traditional security tools that focus on infrastructure protection, DSPM solutions continuously discover, classify, and monitor sensitive data across an organization's entire data estate.
DSPM platforms provide security teams with comprehensive visibility into where sensitive data resides, who can access it, how it's being used, and whether appropriate safeguards are in place. This data-centric approach has become essential as enterprises grapple with data sprawl across multi-cloud environments, SaaS applications, and increasingly complex IT infrastructures.
Why DSPM Matters Now
The explosion of cloud adoption has fundamentally changed how data is stored and accessed. Research indicates that 80-84% of enterprises now maintain a hybrid or multi-cloud infrastructure. This massive migration created unprecedented challenges for security teams trying to maintain visibility and control over sensitive information.
Traditional perimeter-based security controls simply cannot keep pace with modern data architectures. Sensitive information now flows freely across AWS, Azure, Google Cloud, and countless SaaS platforms, each with their own security models and potential blind spots. DSPM emerged specifically to address these gaps, providing the automated discovery and classification capabilities that manual processes fail to deliver at scale.
The Cost of Data Breaches Driving Investment
Financial impact metrics have transformed DSPM from an optional capability to a business imperative. According to IBM's 2025 Cost of a Data Breach Report, the global average breach cost reached $4.44 million, while US organizations faced record expenses of $10.22 million per incident.
Organizations using extensive AI and automation in security operations saved $1.9 million in breach costs while reducing breach lifecycles by 80 days. These compelling economics are driving CISOs to prioritize data security investments that deliver measurable ROI through breach prevention and rapid containment.
The DSPM Market Landscape in 2026
Market Size and Growth Projections
The DSPM market is experiencing explosive growth as organizations confront unprecedented data sprawl across multi-cloud environments.
According to the Future Market Insights 2025–2035 Report, the global DSPM solutions market is valued at USD 1.1 billion in 2025 and is projected to reach USD 1.9 billion by 2035, growing at a CAGR of 5.1%. While market valuations vary based on methodology, with some aggressive estimates reaching $2 billion as early as 2026, the long-term trajectory confirms that data-first security is no longer an emerging niche but a fundamental enterprise requirement.
This growth is being supercharged by a critical AI Oversight Gap. According to the Kiteworks 2026 Forecast Report, only 36% of organizations have the technical visibility to track where that data is actually being processed or trained. This disconnect—the inability to track sensitive data as it flows into autonomous AI agents—has made DSPM the essential "nervous system" for modern security stacks, as firms race to close the gap between AI adoption and data accountability.
US Market Leadership
North America dominates DSPM market distribution, accounting for approximately 40% of global revenue in 2024. The United States leads this adoption due to several key factors:
- Stringent regulatory requirements including HIPAA, CCPA, and industry-specific compliance frameworks
- High concentration of enterprise cloud adoption and digital transformation initiatives
- Significant breach costs averaging $10.22 million per incident in US organizations
- Advanced cybersecurity awareness among executive leadership and boards of directors
Key Drivers Reshaping the US DSPM Market
Accelerated Cloud Migration
Cloud migration patterns fundamentally altered enterprise data architectures, creating unprecedented demand for DSPM capabilities.
The majority of enterprise workloads now operate in public clouds, marking an inflection point where DSPM growth parallels infrastructure migration velocity.
Regulatory Compliance Mandates
Stringent data protection regulations established non-negotiable requirements for data visibility and governance capabilities. GDPR, HIPAA, CCPA, and emerging AI-specific frameworks force organizations to demonstrate comprehensive data inventory and classification capabilities.
Compliance automation has become a primary purchase driver, with platforms mapping security postures directly to regulatory frameworks.
The Infrastructure-to-Data Security Paradigm Shift
Security architectures evolved from infrastructure-first to data-first approaches as cloud-native applications distributed sensitive information across ephemeral containers, serverless functions, and microservices. Traditional Cloud Security Posture Management (CSPM) tools secured cloud configurations but lacked visibility into data contents, access patterns, and sensitivity classifications.
AI Adoption Amplifying Data-First Requirements
AI adoption patterns amplified data-first security requirements significantly. 97% of AI-related breaches occured in organizations lacking proper access controls.
DSPM platforms addressing AI data governance, and training dataset classification became essential as 72% of organizations deployed generative AI either extensively or sparingly. These solutions ensure that innovation does not outpace security, governance, or trust.
Essential DSPM Capabilities for 2026
Continuous Discovery and Classification at Scale
Modern DSPM platforms must automatically discover and classify sensitive data across all environments without manual intervention. Leading solutions provide real-time visibility into sensitive data across cloud, SaaS, and on-premises systems through agentless architectures that analyze metadata and content patterns.
Effective classification goes beyond simple RegEx patterns to incorporate machine learning models that learn organizational data patterns. Advanced platforms offer confidence scoring to validate detections, custom classifiers for industry-specific data types, and data previews to prevent false positives from derailing response efforts.
.png)
Contextual Risk Analysis
Thousands of sensitive data findings become unactionable if treated equally. Modern DSPM platforms combine data sensitivity with identity access patterns, environment exposure, and surrounding misconfigurations or vulnerabilities to prioritize real risks.
Leading tools create security dashboard showing which data faces genuine risk based on actual attack paths. For example, a data store that's publicly accessible, contains payment card information, and is reachable from a compromised workload receives critical priority, while an isolated staging bucket with similar data receives lower priority.
Automated Remediation Workflows
Discovery without action delivers limited value. Effective DSPM solutions integrate with systems that automatically correct risky configurations or excessive access.
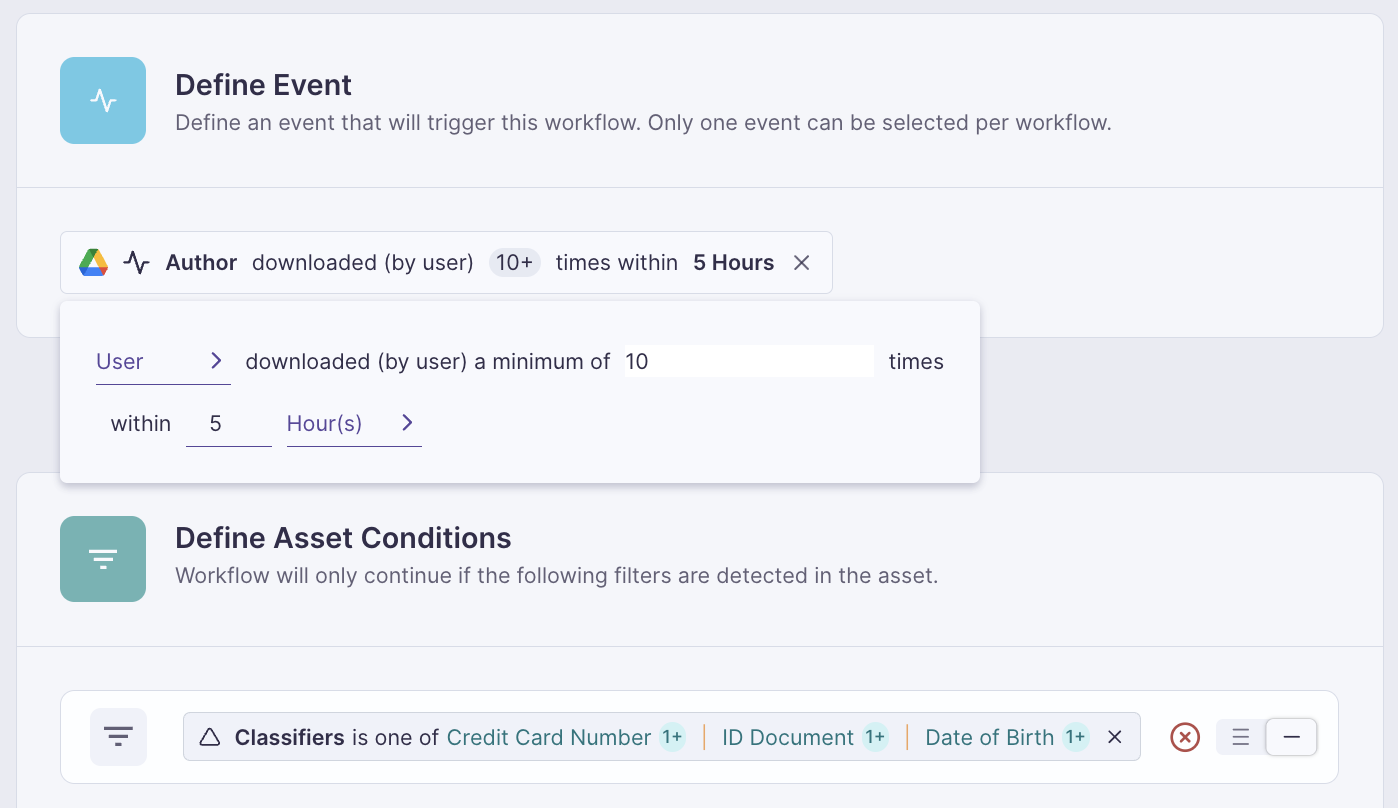
Organizations implementing automated remediation see dramatically reduced mean time to remediation (MTTR) for critical data risks. Policy-as-code approaches enable teams to define and enforce data security policies through infrastructure-as-code guardrails and CI/CD policy engines.
Integration and Scalability
Seamless connections to existing security infrastructure prove essential for effective DSPM deployment. Leading platforms integrate with tools to route alerts and remediation workflows directly into teams' existing processes.
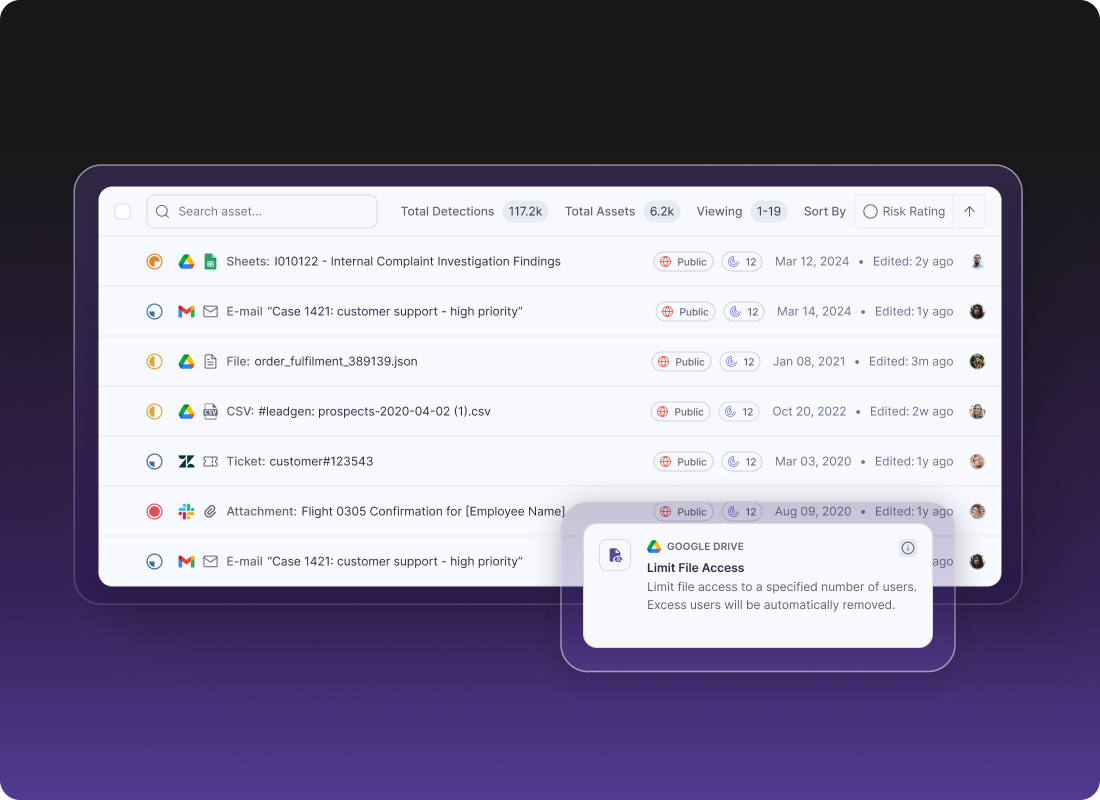
Why Metomic for DSPM in the US
Metomic provides comprehensive data security posture management designed specifically for modern cloud and SaaS environments. Our platform helps US enterprises achieve complete visibility into sensitive data across their entire technology stack while maintaining compliance with HIPAA, CCPA, and other critical regulatory frameworks.
Key Metomic Capabilities
Metomic delivers continuous discovery and classification of sensitive data across SaaS applications, providing security teams with real-time visibility into how information flows through modern collaboration tools. Our platform identifies data security risks including oversharing, external access, and compliance violations automatically.
Automated remediation workflows enable teams to respond quickly to data security incidents without disrupting business operations. Integration with existing security infrastructure ensures Metomic findings flow seamlessly into established workflows and ticketing systems.
Getting Started with Metomic
Organizations implementing Metomic benefit from rapid deployment that delivers initial visibility within hours rather than weeks. Our agentless architecture connects directly to SaaS application APIs without requiring software installation or complex configuration.
Contact Metomic today to learn how our DSPM platform can help your organization achieve comprehensive data security posture management across cloud and SaaS environments while maintaining compliance with evolving regulatory requirements.
Conclusion
DSPM has evolved from an emerging category to an essential component of modern cloud security strategies. As data continues expanding across multi-cloud environments and regulatory requirements intensify, organizations require automated solutions that provide comprehensive visibility, accurate classification, and effective remediation capabilities.
The US market leads global DSPM adoption, driven by stringent compliance requirements, high breach costs, and advanced cloud maturity. Organizations implementing DSPM solutions now position themselves to protect sensitive data effectively while enabling secure innovation and maintaining customer trust.
Success with DSPM requires selecting solutions that match organizational requirements, integrating effectively with existing security infrastructure, and establishing clear governance policies that balance security with business enablement. As the market continues evolving through 2030, DSPM will remain central to data protection strategies across all industries. With Metomic you can get ahead of the curve. To get a free risk assessment, contact our friendly team.


.png)
