DSPM Solutions in Europe: Complete Guide for 2026
Europe's regulatory landscape is reshaping how organizations approach data security. With GDPR fines surpassing €5.88 billion and new frameworks like DORA and NIS2 now in force, European CISOs are turning to DSPM as a strategic priority.

DSPM Solutions in Europe: Complete Guide for 2026
Europe's regulatory landscape is reshaping how organizations approach data security. With GDPR fines surpassing €5.88 billion and new frameworks like DORA and NIS2 now in force, European CISOs are turning to DSPM as a strategic priority.

Main Takeaways from This Article
- By 2026, Gartner projects that 20% of businesses will prioritize DSPM technologies to discover and secure data repositories across multi-cloud environments.
- DORA became fully applicable on January 17, 2025, requiring over 22,000 financial entities across Europe to demonstrate comprehensive ICT risk management and third-party oversight.
- The UK's Cyber Security and Resilience Bill, currently progressing through Parliament, will expand the scope of regulated entities to include managed service providers, data centers, and critical suppliers for the first time.
- Western Europe and the US will account for more than 70% of global information security spending in 2025, according to IDC, with GDPR and the EU AI Act creating demand for continuous monitoring capabilities that traditional tools cannot provide.
- NIS2 implementation remains fragmented, with 13 of 27 EU member states yet to transpose the directive into local law as of August 2025, creating compliance complexity for organizations operating across multiple jurisdictions.
What is DSPM (Data Security Posture Management)?
Data Security Posture Management (DSPM) represents a fundamental shift in how organizations approach cloud data security. Unlike traditional security tools that focus on infrastructure protection, DSPM solutions continuously discover, classify, and monitor sensitive data across an organization's entire data estate.
DSPM platforms provide security teams with comprehensive visibility into where sensitive data resides, who can access it, how it's being used, and whether appropriate safeguards are in place. This data-centric approach has become essential as enterprises grapple with data sprawl across multi-cloud environments, SaaS applications, and increasingly complex IT infrastructures.
Why DSPM Matters in Europe Now
The explosion of cloud adoption has fundamentally changed how data is stored and accessed. Research indicates that 80-84% of enterprises now maintain a hybrid or multi-cloud infrastructure. This massive migration created unprecedented challenges for security teams trying to maintain visibility and control over sensitive information.
Traditional perimeter-based security controls simply cannot keep pace with modern data architectures. Sensitive information now flows freely across AWS, Azure, Google Cloud, and countless SaaS platforms, each with their own security models and potential blind spots. DSPM emerged specifically to address these gaps, providing the automated discovery and classification capabilities that manual processes fail to deliver at scale.
The Cost of Data Breaches Driving Investment
Financial impact metrics have transformed DSPM from an optional capability to a business imperative. According to IBM's 2025 Cost of a Data Breach Report, the global average breach cost reached $4.44 million, while organizations using extensive AI and automation in security operations saved an average of $1.9 million in breach costs.
For European companies, the calculus extends beyond direct breach costs. GDPR enforcement continues to intensify. According to the CMS GDPR Enforcement Tracker Report, total fines since May 2018 have reached approximately €5.65 billion as of March 2025, with 2,245 fines recorded. Germany reported 27,829 data breach notifications in 2024, making it the second-highest in Europe, while Denmark leads per capita in breach notifications (DLA Piper). The Irish Data Protection Commission alone has imposed fines exceeding €3.5 billion, including the record-breaking €1.2 billion penalty against Meta in 2023 for international data transfers.
The European DSPM Market Landscape in 2026
Market Size and Growth Projections
The DSPM market is experiencing significant growth as organizations confront unprecedented data sprawl across multi-cloud environments. Market valuations vary by methodology, with estimates ranging from $1.2 billion to $2 billion in 2025, growing at a CAGR between 16.5% and 25% annually through 2033. Some projections estimate the market could reach $10 billion by 2033.
Europe represents a significant growth market for DSPM, driven by GDPR, the EU AI Act, and emphasis on data sovereignty and privacy-by-design approaches. The European market is characterized by an emphasis on data sovereignty and privacy-by-design approaches, with GDPR and the EU AI Act creating demand for continuous monitoring capabilities that position DSPM solutions as particularly relevant. The European cloud data security market (which includes DSPM as a core component) is projected to reach roughly $2.61 billion by 2030.
European Regulatory Leadership
Europe's position in DSPM adoption is driven by several distinct factors. The regulatory environment differs substantially from other regions, with multiple overlapping frameworks creating complex compliance requirements that favor comprehensive data visibility solutions.
The cumulative weight of GDPR, DORA, NIS2, and emerging AI regulations has created a compliance landscape where understanding data flows across borders has become a strategic necessity rather than a nice-to-have capability. Organizations operating across multiple European jurisdictions face particular challenges, as national implementations of directives like NIS2 vary significantly in reporting requirements, enforcement approaches, and sector-specific rules.
Key Drivers Reshaping the European DSPM Market
DORA: A New Era for Financial Services
The Digital Operational Resilience Act (DORA) became fully applicable on January 17, 2025, marking the most significant regulatory overhaul of financial technology infrastructure in a decade. DORA applies to approximately 22,000 financial entities across Europe, including banks, insurance companies, investment firms, payment institutions, crypto-asset service providers, and their ICT third-party providers.
The regulation introduces uniform requirements for ICT risk management, incident reporting, operational resilience testing, third-party risk management, and information sharing. Financial entities must establish automated monitoring systems capable of detecting anomalies and triggering alerts within hours, following standardized reporting templates that enable cross-sector analysis.
For CISOs in financial services, DORA's third-party oversight requirements are particularly demanding. Organizations must assess and monitor risks associated with ICT service providers, formalize contractual agreements outlining service expectations and compliance requirements, and maintain registers of information on ICT third-party arrangements. Critical ICT third-party providers are subject to direct oversight by European Supervisory Authorities, who began the designation process in 2025.
Non-compliance carries substantial penalties. Organizations can face fines up to 2% of global annual turnover or €10 million, whichever is higher. Critical third-party ICT providers may face fines as high as €5 million for failing to comply.
To learn more about DORA, read our "Complete guide to DORA".
NIS2: Expanded Scope, Fragmented Implementation
The NIS2 Directive aims to strengthen cyber resilience across 18 critical sectors in the EU, establishing baseline requirements for cybersecurity risk management and incident reporting. However, implementation has proven challenging.
According to the European Cyber Security Organisation (ECSO) NIS2 Transposition Tracker, as of mid-2025, only 16 EU and EEA countries had fully adopted national laws transposing NIS2 requirements. In May 2025, the European Commission issued formal reasoned opinions to 19 Member States for failing to fully transpose the directive, including major economies such as Germany, France, and Spain.
This fragmented implementation creates operational challenges for organizations operating across borders. Reporting obligations vary significantly across member states. Cyprus, for example, requires early warnings within six hours of detection, well ahead of NIS2's 24-hour requirement. Definitions of significant incidents, reporting thresholds, and supervisory structures differ, increasing the administrative burden for cross-border entities.
NIS2 introduces penalties of up to €10 million or 2% of global annual turnover for essential entities, with management bodies personally accountable for compliance. Some countries, including Poland and Malta, have introduced executive liability provisions that exceed the directive's minimum requirements.
The UK's Cyber Security and Resilience Bill
The UK Cyber Security and Resilience Bill was introduced to Parliament on November 12, 2025, and represents the first major overhaul of UK cybersecurity legislation since Brexit. The bill updates the Network and Information Systems Regulations 2018 and is expected to receive Royal Assent in 2026.
The bill significantly expands the scope of regulated entities to include managed service providers, data center operators above specified capacity thresholds, and critical suppliers whose disruption could significantly impact the economy or day-to-day functioning of society. This means organizations that previously operated outside NIS regulations may find themselves brought within scope for the first time.
Key provisions include enhanced incident reporting requirements, expanded regulatory powers, and the ability for the Secretary of State to direct regulated entities to take steps that mitigate imminent threats to national security. The bill introduces potential fines of £100,000 per day for failing to act against relevant threats.
While the bill aligns with NIS2 in many respects, including expansion of scope and stricter incident reporting, there are notable divergences. The UK bill applies to fewer sectors and does not impose personal liability for management, taking what the government describes as a tailored approach focused on the most critical sectors.
Regional Perspectives: Nordic Countries, Germany, and France
The Nordic countries have adopted a minimalistic approach to NIS2 implementation, closely following the directive's baseline requirements without adding significant national-specific obligations. Denmark implemented the directive with compliance required from July 1, 2025, while Finland required risk management approaches to be in place by July 8, 2025. Sweden's implementation entered into force on January 15, 2026.
Nordic countries rank among the most cyber-secure globally, with strong institutions, public-private collaboration, and consistent regulatory frameworks. Finland, Sweden, Denmark, and Norway are noted for substantial investment in information security, strict data protection legislation, and public awareness programs.
Germany’s NIS2 Implementation Act officially entered into force on December 6, 2025, following a significant delay due to the 2025 federal election cycle. With the law now active, approximately 30,000 German organizations are facing immediate compliance requirements, including a mandatory registration with the Federal Office for Information Security (BSI) via a new portal. This regulatory shift is a primary driver behind surging cybersecurity budgets in Germany, as companies move beyond legacy perimeters to prioritize Zero Trust architecture, supply chain security, and continuous SaaS security audits to mitigate board-level liability.
France remains in the legislative process for NIS2 implementation. The EU Commission's Digital Omnibus package proposes streamlining incident reporting through a "report once, share many" approach, which would establish a single incident reporting mechanism covering NIS2, GDPR, eIDAS, DORA, and CER Directive.
AI Adoption Amplifying Data-First Requirements
AI adoption patterns have amplified data-first security requirements significantly. According to IBM's 2025 Cost of a Data Breach Report, 97% of organizations that experienced an AI-related security incident lacked proper AI access controls. Additionally, 63% of breached organizations either don't have an AI governance policy or are still developing one.
Shadow AI, where employees use unapproved AI tools without IT oversight, was a factor in 20% of breaches studied, adding an average of $670,000 to breach costs. These incidents led to more personally identifiable information (65%) and intellectual property (40%) being compromised compared to the global average.
The EU AI Act adds another layer of compliance requirements, creating demand for solutions that can address AI Act compliance while maintaining data visibility. DSPM platforms addressing AI data governance and training dataset classification have become increasingly relevant as 72% of organizations have deployed generative AI either extensively or sparingly.
Essential DSPM Capabilities for 2026
Continuous Discovery and Classification at Scale
Modern DSPM platforms must automatically discover and classify sensitive data across all environments without manual intervention. Leading solutions provide real-time visibility into sensitive data across cloud, SaaS, and on-premises systems through agentless architectures that analyze metadata and content patterns.
Effective classification goes beyond simple RegEx patterns to incorporate machine learning models that learn organizational data patterns. Advanced platforms offer confidence scoring to validate detections, custom classifiers for industry-specific data types, and data previews to prevent false positives from derailing response efforts.
.png)
Contextual Risk Analysis
Thousands of sensitive data findings become unactionable if treated equally. Modern DSPM platforms combine data sensitivity with identity access patterns, environment exposure, and surrounding misconfigurations or vulnerabilities to prioritize real risks.
Leading tools create security dashboards showing which data faces genuine risk based on actual attack paths. A data store that's publicly accessible, contains payment card information, and is reachable from a compromised workload receives critical priority, while an isolated staging bucket with similar data receives lower priority.
Automated Remediation Workflows
Discovery without action delivers limited value. Effective DSPM solutions integrate with systems that automatically correct risky configurations or excessive access. Organizations implementing automated remediation see dramatically reduced mean time to remediation (MTTR) for critical data risks. Policy-as-code approaches enable teams to define and enforce data security policies through infrastructure-as-code guardrails and CI/CD policy engines.
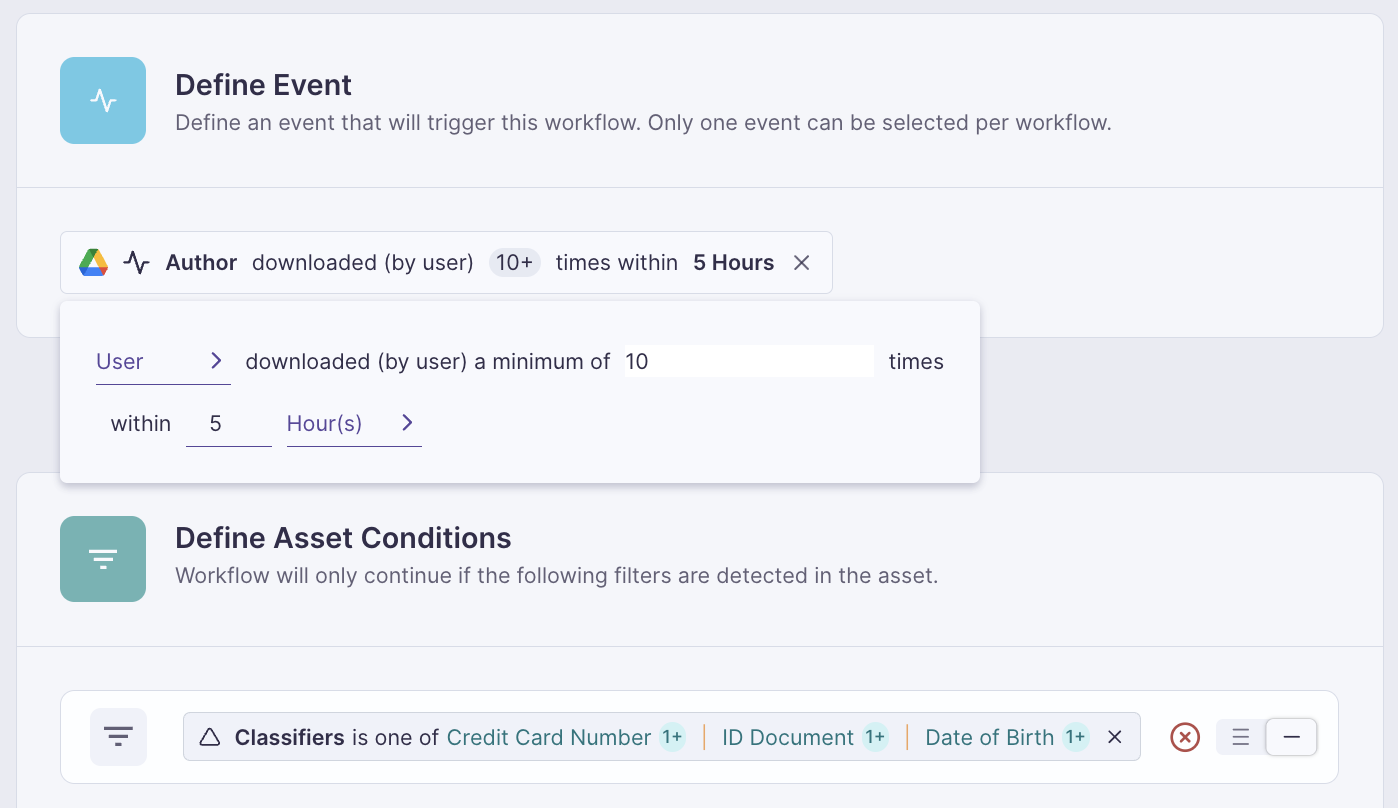
Integration and Scalability
Seamless connections to existing security infrastructure prove essential for effective DSPM deployment. Leading platforms integrate with tools to route alerts and remediation workflows directly into teams' existing processes. For European organizations, integration capabilities that support compliance documentation and audit trail generation are particularly valuable given the multiple overlapping regulatory requirements.
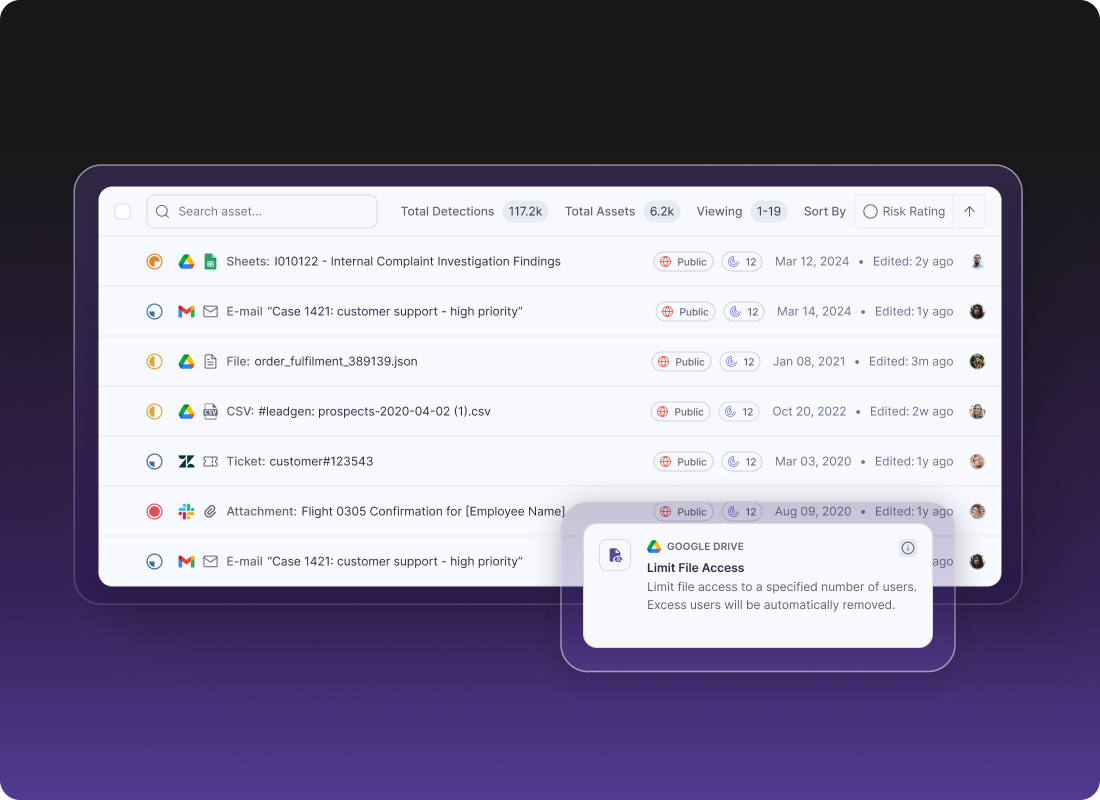
Why Metomic for DSPM in Europe
Metomic provides comprehensive data security posture management designed specifically for modern cloud and SaaS environments. Our platform helps European enterprises achieve complete visibility into sensitive data across their entire technology stack while maintaining compliance with GDPR, DORA, NIS2, and other regulatory frameworks.
Key Metomic Capabilities
Metomic delivers continuous discovery and classification of sensitive data across SaaS applications, providing security teams with real-time visibility into how information flows through modern collaboration tools. Our platform identifies data security risks including oversharing, external access, and compliance violations automatically.
Automated remediation workflows enable teams to respond quickly to data security incidents without disrupting business operations. Integration with existing security infrastructure ensures Metomic findings flow seamlessly into established workflows and ticketing systems.
Getting Started with Metomic
Organizations implementing Metomic benefit from rapid deployment that delivers initial visibility within hours rather than weeks. Our agentless architecture connects directly to SaaS application APIs without requiring software installation or complex configuration.
Contact Metomic today to learn how our DSPM platform can help your organization achieve comprehensive data security posture management across cloud and SaaS environments while maintaining compliance with evolving European regulatory requirements.
Conclusion
DSPM has evolved from an emerging category to an essential component of modern cloud security strategies for European organizations. As data continues expanding across multi-cloud environments and regulatory requirements intensify, organizations require automated solutions that provide comprehensive visibility, accurate classification, and effective remediation capabilities.
Europe's regulatory environment, with GDPR enforcement continuing at pace, DORA now in force for financial services, NIS2 implementation progressing (if unevenly), and the UK Cyber Security and Resilience Bill expected to become law in 2026, creates both challenges and opportunities. Organizations implementing DSPM solutions now position themselves to protect sensitive data effectively while enabling secure innovation and maintaining customer trust.
Success with DSPM requires selecting solutions that match organizational requirements, integrating effectively with existing security infrastructure, and establishing clear governance policies that balance security with business enablement. As the market continues evolving through 2030, DSPM will remain central to data protection strategies across all industries. With Metomic you can get ahead of the curve. To get a free risk assessment, contact our friendly team.


.png)
